This is serious now. Our Expert Bitcoin Security level is specifically aimed at people who have serious investment amounts that they need to safeguard for decades. What “serious” means to you will be different to someone else, but it’s usually $1,000 or more. Sometimes considerably more upwards of tens, hundreds of thousands or even millions of dollars. We’re not joking around now boys and girls.
Just like with anything that involves serious amounts of money it does get more complex, more costly and more difficult now that we’re at the highest level. Frankly, if you’re not willing to put in the time to study and get good at security then you shouldn’t be storing large amounts of wealth in Bitcoin.
We’re dedicated to teaching, simply, how to do everything Bitcoin but you still need to put in the time to read, practice and Learn About Bitcoin yourself. If you don’t follow the steps below then don’t be shocked when you get hacked and loose all your funds.
That being said, do know that it’s absolutely possible to have a state of the art setup that’s created and maintained by you for serious investments. Bitcoin gives you that option and although it might take some learning, it completely removes all trusted third parties and allows you full self sovereignty over your funds.
Note: This Security guide is for “Expert Levels” which are people with “Serious Investment” amounts of funds. If you’re securing smaller amounts, please see our Beginner Bitcoin Security and Advanced Bitcoin Security level guides
Contents
Key Expert Bitcoin Security Points
- Beginner Security: Ensure you do everything in our Beginners Guide To Bitcoin Security
- Advanced Security: Ensure you do everything in our Advanced Guide To Bitcoin Security
- Verify Files And PGP Key Signatures: Don’t install unverified wallets or files
- Expert Hardware Wallet Security: Consider using Trick PINs or Decoy Wallets
- Multisig Wallets: Learn about, setup and start using Multisig Wallets
- Multi Vendor Hardware Wallet Setups: Consider using multi vendor Multisig wallets
- Expert Computer Security: Get a dedicated device for your Software Wallet and isolated it
- IRL Security Best Practices: Stay anon, avoid in person trades and keep good company
Expert Bitcoin Security
Firstly, you can get a full run down on what each of our levels entail and where you might fit into them by looking at our Understanding Bitcoin piece or this overview table below.
For this Expert Bitcoin security guide we are only targeting people that have serious investment funds. For most people, this is an amount that represents either significant portion of, or their entire life savings and is unacceptable to loose, so security precautions get pushed to the extreme.
| Level | Beginner | Advanced | Expert |
|---|---|---|---|
| Funds Amount | Pocket Money | Savings Account | Serious Investments |
| Exchange Type | Non-KYC | Non-KYC | Non-KYC |
| Wallet Type | Software (Hot) / Hardware (Cold) | Hardware (Cold) | Hardware (Cold) |
| Signature Type | Single Signature | Single Signature | Multisig |
| Key Custody | Self Custody | Self Custody | Self Custody |
| Key Backup | Laminated Paper | Laminated Paper | Metal Seed Plate |
| Key Locations | 1+ | 2+ | 2+ |
| Key Security | None | Fire Proof Safe | Multiple Methods |
| Own Full Node | No | Yes | Yes |
| Electrum Server | Public Electrum toggle_on | Private Electrum toggle_on | Private Electrum toggle_on |
| Tor | No | Yes | Yes |
Our top priorities for this site is to help everyone learn how to safely and privately buy, use, invest and grow wealthy with Bitcoin, so know that this piece is just the start of our security information.
As Expert level security is quite a bit more nuanced and complicated, this guide isn’t so much focused on telling you exactly how to use all the various possibilities, but more about beginning the conversation on them.
We’ll be adding and expanding on each of the below points in much more detail as time goes on with their own separate pieces and how to guides where needed.
If you haven’t already, please also make sure you’ve already read and done the security steps outlined in our Advanced Bitcoin Security guide which broadly include:
- Use A Hardware Wallet: Use a Hardware Wallet and ensure it’s bought anonymously
- Advanced Wallet Security: Ensure 2+ backups at 2+ locations with proper location security
- Balancing Security And Complexity: Consider extra security measures carefully
- Use Your Own Full Bitcoin Node: Buy or build a full node and connect your wallet to it
- Advanced Computer Security: Ensure your network, mobile and PC are properly secured
- Test Your Backups Regularly: Routinely test your backup ensuring you can spend funds
- Security Through Anonymity: Don’t tell friends, family or social networks you own bitcoin
Verify Files And PGP Key Signatures
The first thing we’re going to cover is about being much more cautious about the software you use and download. While we’ve recommended Bitcoin Wallets like Sparrow Wallet in our previous guides, it’s now critical that you make sure you’re verifying the software files and PGP key signature each and every time you download or update the application.
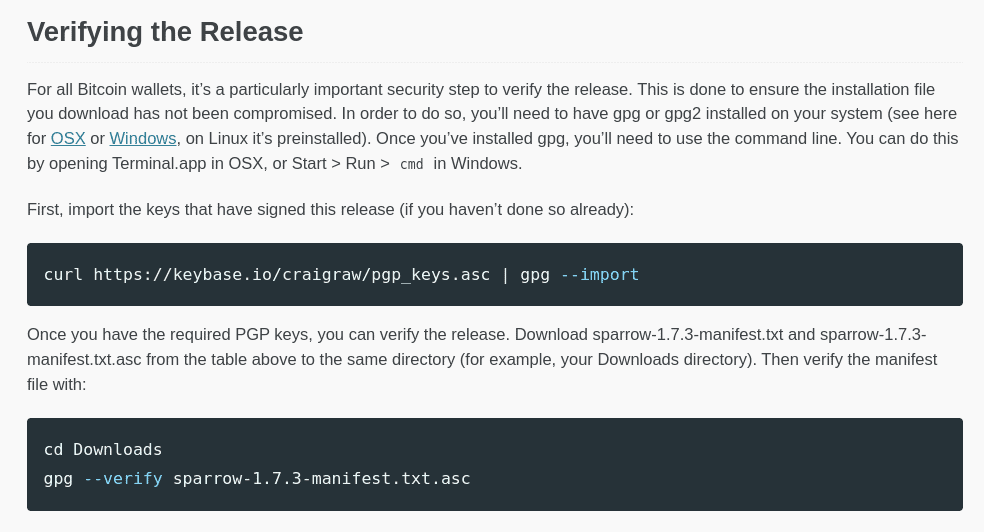
This procedure is generally the same for most programs, but can differ slightly depending on how the developers set things up. Either way it’s broken down into two parts. The first is verifying the signature of the manifest file while the second is checking the binary checksums.
Verifying the signature is done by confirming that the PGP Key signatures given on the website match the ones in the downloaded files. To do this you have to first download and import the developers PGP Key (in the image above it’s Craig Raw) and then do the signature verification check as shown in their example.
The second part of this goes even deeper and checks the binary files to make sure that the checksums match up. Once again you follow their instructions and if you get an “OK” back then you know the two checksum hashes match.
If it sounds like we’re glossing over the details a bit here, it’s because we have many guides already published with the steps in them. For example, here is the guide to downloading, verifying and setting up Sparrow:
- How To Install Sparrow Wallet On Ubuntu And Verify It’s Secure
- How To Install Sparrow Wallet On Windows And Verify It’s Secure
Only once the update or new download passes these tests should you install the software.
Expert Hardware Wallet Security
In our Advanced Security Guide we covered the differences between your Mnemonic Sentence, Passphrase, Hardware Wallet and PIN. At the Expert level these things become less relevant as you should be learning about and migrating to a Multisignature setup. We’ll cover that in more detail below, but first we are going to cover some more expert level Hardware Wallet security.
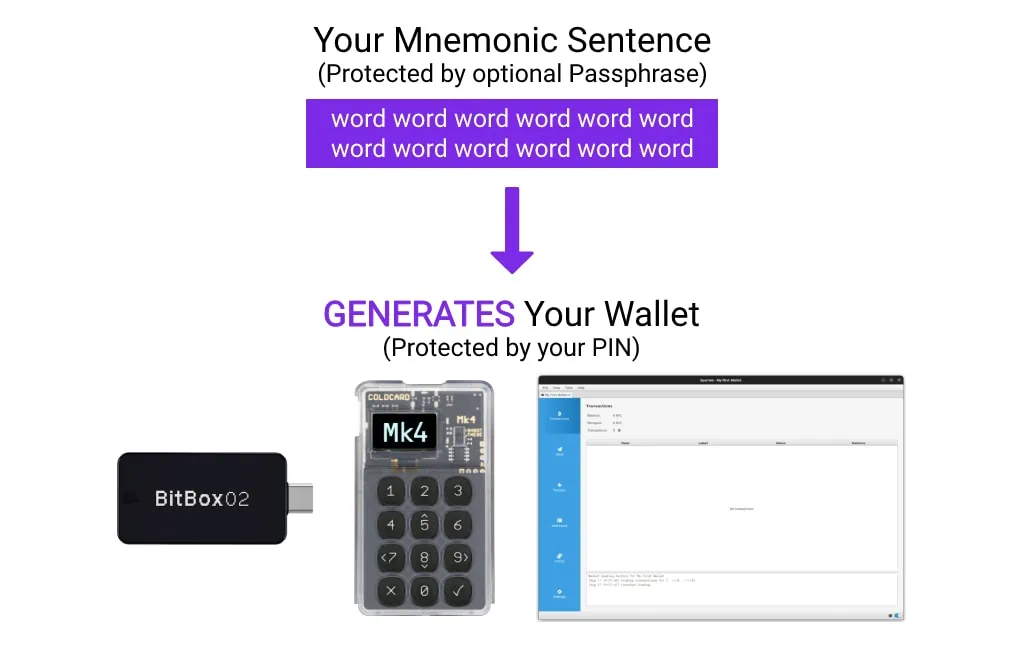
Trick, Brick & Duress PINs
Some Hardware Wallets such as the COLDCARD Mk4 have various Trick PINs such as what’s called a Duress PIN that helps in the event of a physical attack. This is where a robber is literally standing over you with a weapon and threatening your life while you’re forced to open your Hardware Wallet.
You may define an optional “duress PIN code”. If anyone enters that PIN code, instead of the “real” PIN code, nothing special is shown on the screen and everything operates as normal… However, the bitcoin key generated is not the main key. It is effectively a completely separate wallet!
COLDCARD
This separate wallet should have some “decoy” funds in it so that you can plausibly show the attacker and they can steal that rather than the funds in your main – and likely much larger – wallet.
How much should you have in your decoy wallet? That’s up to you. But. It should be an amount that will satisfy an attacker. If you’re sitting there in a Rolex with 5 lambos out the front and try and claim your main wallet has $1,000 of BTC in it… well then that’s probably not going to work.
Trick PINs can also do other actions such as completely brick the Hardware Wallet. This might not be the best idea if an attacker is standing over you, but perhaps you might want to do this if someone attempts to confiscate your Hardware Wallet from you. Some even support a countdown function where it bricks the device after a certain time period.
Whatever your game plan is, there are lots of various options available due to the unique digital nature of Bitcoin. While we talk about this just like any other technology it’s always worth reiterating that this type of custom and granular control is completely unprecedented for asset custody. Imagine trying to “brick” $1,000,000 worth of gold or trick a thief into stealing your smaller stash of gold that’s somehow in the exact same safe? Bitcoin truly is a step change in money!
Decoy Wallets & BIP39 Passphrases
Closely related to Trick PINs, but very different is Passphrases. While the PIN is what you enter into your Hardware Wallet to unlock it, Passphrases are the 13th or 25th words that get chosen by you and are added onto your Mnemonic Sentence.
They don’t have to be a specifically defined word like the Mnemonic Sentence, but instead can be anything you invent just like a regular password. It’s recommended that, like your passwords, you make it as long, strong and as random as possible too.
Passphrases get added onto your Mnemonic Sentence and create an entirely new wallet separate to your normal 12/24 word Mnemonic Sentence wallet. This separate wallet can have infinite Bitcoin Addresses, transactions and so on with its own balance and unique transaction history. Maybe you send and receive a bunch of transactions to/from it as well as putting a plausible amount in there to make sure it looks “real”.
Either way, this decoy wallet is tied to that Passphrase you set and you can have an unlimited number of different Passphrases that get added onto your Mnemonic Sentence to create unlimited unique wallets all with their own history and balance. For example if you were a real baller with 5 BTC you could set it up like this:
- 12 Words: 1 BTC
- 12 Words + Passphrase 1: 1 BTC
- 12 Words + Passphrase 2: 1 BTC
- 12 Words + Passphrase 3: 1 BTC
- 12 Words + Passphrase 4: 1 BTC
Is this a good idea? No, because now you have a Mnemonic Sentence and four separate Passphrases to remember! But it illustrates how each Passphrase creates a brand new wallet.
How you use this power is only limited by your imagination, but having a Passphrase on a Single Signature wallet is an excellent way of ensuring your Mnemonic Sentence is protected in case anyone ever steals it. The downside as discussed in our Advanced Security Guide is that you now effectively have a 2-of-2 Multisignature wallet with 2 single points of failure.
Air Gaped & Other Connectivity Options
Finally let’s talk about Air Gaped Hardware Wallets, how they work, their pros and cons. An Air Gaped Hardware Wallet means it has no physical data connection to the computer you’re using for the Software Wallet component. Instead you use other connectivity methods to bridge the “air gap”.
The theory is that this makes the Hardware Wallet more secure as it can’t be hacked if it’s not actually connected to anything. However data still needs to flow back and forth between the Hardware Wallet and the Computer that’s creating and broadcasting the Bitcoin Transaction.
When you want to Send Bitcoins, the computer creates what’s called a Partially Signed Bitcoin Transaction (PSBT). This transaction data is then transmitted to the Hardware Wallet so it can use your Private Key to sign it. Then you have to transmit that signed transaction data back again. As such, the entire security of the Hardware Wallet depends on the integrity of that data being exchanged. If it’s been compromised, then you’re still in trouble.
Just with any other type of security, air-gaped is not a panacea and doesn’t just magically make your crypto “hacker proof”. An internationally famous example of air-gaped computers getting hacked was the Stuxnet malware that took down a uranium enrichment facility in Iran in 2010.
We have a full, super in depth piece dedicated to Air Gapped Hardware Wallets here. As such, we won’t dive too deeply into the topic now, but whether you’re transmitting data to the Hardware Wallet via QR Code, microSD card or a more normal (non air-gaped) USB connection there is still data going back and forth.
If someone infects your computer and takes control of your software wallet, it won’t matter how the maliciously created transaction data is transferred to the Hardware Wallet.
What matters is how that Hardware Wallet receives, inspects and sanitizes it. If it’s not doing this properly, then an air-gaped Hardware Wallet can 100% still get hacked. So be sure to understand that something being “air-gaped” doesn’t make it bullet proof.
Multisignature Wallets
OK. We’ve increased the security of a Single Signature wallet to its maximum… now what? Obviously from the heading it’s moving to a Multisignature wallet setup.
When we’re talking about serious investment funds multisig is very heavily recommended. We want to remove as many single points of failure as possible whilst also ensuring that individual components like seed phrases are still safe and Multisig helps with this and more.
At this level of funds it’s also common to plan for what happens when you die or how you might be passing the funds onto your children or other family members. While this is possible using single signature wallets, there isn’t as much flexibility available and it’s kind of an all or nothing type of thing.
What Is A Multisignature Wallet?
A multisignature or “multisig” wallet is one that is setup with multiple Private Keys rather than just one. This means that when you want to sign a transaction you need some threshold of keys all combined together rather than just one key.
A common example is a 2-of-3 setup, where there are a total of 3 private keys, but only any 2 are required to successfully sign a transaction and spend the funds. You can also have 2-of-2, 3-of-5 or even 7-of-9.
Why Should You Use Multisig?
The main reason to use a Multisig wallet is to ensure that you have no single points of failure. It also helps stop attackers from being able to spend your bitcoins if they steal one of your keys or force you to unlock one of your Hardware Wallets. That being said there’s also many other use cases such as:
- Lightning Channels: Creation of a Lighting Network channel (2-of-2)
- Escrow Funds: A buyer, seller and third party that can arbitrator or resolve disputes (2-of-3)
- Shared Custody Of Funds: You hold 2 keys and someone else holds the 3rd key (2-of-3)
- Business Custody Of Funds: Shared custody of funds for companies or communities both to protect the funds but also to protect the key holders (N-of-M)
While it might seem simple in our description above (just have 3 keys instead of 1!) unfortunately it adds quite a bit more complexity which as we know, is the enemy of good security.
Multisig Increases Complexity
So now that you know what a Multisig Wallet is and why you might use one, what additional complexity requirements are we trading for this extra security?
- Multiple Private Keys: While this is kind of the point of Multisig, you now have 3, 5 or even more keys that you have to deal with which inherently increases complexity
- More Things To Backup: While you only have to store the Mnemonic Sentence (the 12 or 24 words) to backup a single signature wallet, with Multisignature wallets you also have to store the Extended Public Keys (xPubs) as well as the used threshold, derivation path and script type of all key pairs. And yes, an Extended Public Key is different to a Public Key or a Private Key. If you don’t backup all this extra data (of all keys and in all locations) then a loss of a single seed will mean you can no longer receive or spend your funds
- More Complex Backup: As we now need to backup more data than just 12 words, it’s common for Hardware Wallets to use microSD cards to automatically export and store the entire Multisig backup. This means your backup is now at the mercy of how fragile this non-volatile SD memory card is. Maybe it’s a cheap POS and fails after a year… without you knowing. Even if it’s a good quality card, they’re not designed for long term data storage and it may only last a few years depending on how harsh its storage conditions are. Cards stored in extreme heat or that are exposed to moisture, humidity or magnetic fields can all fail very quickly. Even in perfect conditions, it will normally only stay valid for up to 10 years
- More Complex Setup And Recovery: Backing up the wallet isn’t the only more complex thing, setting up the initial wallet and recovering it is also more complex and to make matters worse, most Hardware and Software Wallet makers mostly focus on the Singlesig workflow so there’s less documentation, thought and support in general for it
- Poor Hardware Wallet Support: As Singlesig is more popular and Multisig more complex, there have been many instances over the years where Hardware Wallet manufacturers simply just haven’t supported it as well or haven’t given the Multisig workflow as much scrutiny as they do for Singlesig. This leads to less documentation, support articles and often dumps the problem onto the user rather than the device. For example Trezor supports Multisig, but not on their companion app
When it comes to different security measures that protect your Bitcoin, most of them aren’t a good trade off. They’ll greatly increase complexity without really offering serious (or any!) benefits.
Some also offer benefits to problems that statistically don’t happen very often to people. For example, someone might create a hugely complex seed storage plan to protect against some sophisticated state level attacker… and in the end lock themselves out of their funds.
While Multisig wallets are absolutely more complicated for the Hardware Wallet, the Software Wallet and for you, the added security and benefits they bring are extremely useful and do solve very real and common security issues.
As such, we feel that for serious investment funds and for those who properly educate themselves about these added complexities and how to handle them, Multisig is an invaluable tool to increase security.
Private Key Storage And Security
Last but not least when it comes to Multisig is the storage of the multiple backups. As noted above, these backups don’t just include your Mnemonic Sentence, they each have a copy of all your Extended Public Keys as well as other bits and pieces like derivation paths too.
While this is a downside to Multisig, the upside is that now each one of these keys can be stored in a much more forgiving environment seeing as they’re not longer a single point of failure. For example, you can store one in a bank safety deposit box even though it’s not actually that safe a place in reality:
The contents of safe deposit boxes may be seized under the legal theory of abandoned property. They also may be searched and seized by the order of a court through the issuance of search warrant.
Wikipedia
Even if a robber steals it or the government legally takes it for some reason, your funds are safe as 2 backups are required to actually spend the funds.
As the number of keys you have increases, you will need more secure locations to match. For example a 3-of-5 wallet would need 5 secure backups stored at 5 separate secure locations. You’ll also want to be increasing the security around how you store the backup too. Potential ideas for good storage locations include:
- Home Safe: Lock boxes, strong boxes, fireproof safes that are hidden or bolted down
- Safety Deposit Boxes: Located at a private company (not a bank) with 24/7 security
- Buried Locations: This can be stored somewhere on your property or holiday home
- Hidden Locations: False bottom draws, walls, books or any other item (backups are small!)
- Safe Room: In a secure compartment of a hidden safe room in your house or other property
- Remote Locations: At a holiday home, workplace or families location
If your backup is a microSD card, the sky really is the limit when it comes to hiding places given how small and thin they are. You could literally paint it onto a wall, as in stick it to a wall and plaster / paint over it.
You could hide it in a computer mouse, under a keyboard key cap, the lid of a cookie jar, in or under a floor board, woven into a piece of clothing, inside your alarm clock or even chiselled into any wooden surface and then puttied over.
We recommend you preference places that have 24/7 guards, security camera surveillance, gates and forms of physical security. You’ll also want to consider the locations proximity to one another too. Try and have them physically far away from each other so that it takes time to get there.
For example one can be at your home, one at your parents (4 hour drive away) and one at your holiday home (15 hours drive away). You can also preference places that are only available at certain times (such as banks or your work).
This can help if an attacker puts you under physical duress and demands your funds. You may have 1 key on you and can give them that… but in order actually steal / spend your funds they’ll need to drive to a second or maybe even third location hundreds of kilometers away or that is under more strict surveillance.
While kidnapping or holding someone under duress isn’t unprecedented, doing so is increasingly difficult the longer the ordeal continues. Any way you can put time locks on things or add in extra layers of security that they’ll need to get through hugely increases the likelihood that the overall attack will fail.
This again comes back to our overarching mantra that nothing is 100% secure. The point of good security is to add layer upon layer of security in order to slow down and hopefully stop the attacker at one layer or another. Maybe they can break into your house, but can they also break into a secure company safety deposit box to get the 2nd key? Can they do this while holding you hostage for days? Unlikely.
Multi Vendor Hardware Wallet Setups

The Infinity Hardware Wallet. Source: The real MCU
While you’re setting up a new Multisig wallet, you should also consider potentially making it a multi vendor multisig wallet too.
This is where your various hardware wallets are sourced from different manufacturers. For example, rather than having a 2-of-3 multisig wallet with three BitBox02‘s, you might instead have one BitBox02, one COLDCARD Mk4 and one Foundation Passport.
Hardware Wallet Hardware
Many Hardware Wallets use the same underlying hardware components from the same manufacturer (the STM32 in particular) and as such, might be vulnerable to any bugs or intentional back doors that it has.
This is why it’s important to not just choose any random hardware wallets to pair up. To be most effective, try and pick ones that have totally different MCU and/or Secure Element chips.
This is a highly technical and fascinating topic, which is why we’ve got an entire piece on it where we dig deep into the underlying hardware that some of the most popular Hardware Wallets use.
>> Deep Dive: Why The Brain Of Hardware Wallets Is Actually Their Biggest Weakness
Multi Vendor Pros
Having different hardware devices is an excellent security practice as it allows you to test for and pick up on a number of different security issues that you’d otherwise completely miss.
Say for example BitBox02 pushes out an update that unintentionally messes up how receive addresses are generated. If you have three BitBox02’s in your multisig wallet, then all of them are going to generate the same (incorrect) receive address. You send the funds to “safely store them”, but instead you’ve now lost your bitcoin.
However if this happened in a multi vendor setup, when you compare the receive addresses on the BitBox02 to any of your other vendor hardware wallets they’d be different. This would alert you to something being wrong and hopefully save you from losing any funds.
This type of scenario can also happen when generating your private keys. Maybe the COLDCARD Mk4 has a bug or has been taken over by the government and had a malicious update forced out, resulting in the private key being generated insecurely. As you have different vendors, only 1 of your keys will be compromised and your funds would remain safe.
Whether malicious or unintended, software or hardware, multi vendor setups give you a lot of extra protection and ensures that all devices are always verifying each other constantly.
Multi Vendor Cons
This added protection does come as a small cost in complexity. Having different hardware wallet vendors means you’re:
- Increasing the attack surface area due to using more software
- Increasing complexity as there’s multiple different devices to learn how to use
There’s also the issue of compatibility between the wallets and how well – or if at all – they work together. As noted above, even just having a multisig wallet can result in improper support by a single vendor. So having a multisig setup that uses multiple vendors could potentially cause all sorts of issues!
This means that it’s very important to ensure you do considerable research before just assuming that hardware wallet X, Y and Z will all work perfectly together with each other.
Is Multi Vendor Worth It?
While it’s highly unlikely that you’ll lose your funds due to a rouge government forcing a malicious code update to a popular hardware wallet vendor that backdoors its underlying security somehow, it is a highly critical potential security risk.
The more likely scenario is simply a buggy software release, but in either scenario the results can range from losing some of your funds to losing all of them. As such using multi vendor hardware wallets is something we’d recommend considering.
It certainly isn’t without its added complexity, which itself has its own risk, so we’d also recommend ensuring you’re very comfortable with every device you’re using in your setup beforehand. Make sure you’ve done extensive testing before moving the majority of your funds over and know what you’re getting into.
Expert Computer Security
Upgrading your general computer security is always a good idea, regardless of the amount of funds you’re protecting. So if you haven’t read it already, go back and look at the Beginner Computer Security and Advanced Computer Security measures as they will get you 99% of the way there.
For the expert level though we want to address one of the most common ways people’s Bitcoin Wallets get hacked and their bitcoins stolen. This is by having their main wallet on the same computer that they use for their everyday activities.
Even the most careful user is still going to open emails, look at attachments, click on links, download and install various applications and so on. Maybe they’re safe and secure 999 times out of 1,000. But. It only takes 1 time for things to go south and from there the compromise can happen a thousand different ways.
This is why we recommend taking it up a notch and ensuring you have a completely separate computer dedicated only to your Bitcoin Software Wallet. It should be:
- New(ish): Be new enough to still get current security updates
- Latest OS Version: Have the latest OS installed on it, preferably Linux or Mac
- Encrypted Disk: Ensure the entire drive is encrypted from boot
- Unique & Strong Password: Ensure the password is extra strong and completely unique
- No Other Programs: Have all bloatware and non essential programs removed
- Only Used For Bitcoin: Only have your Software Wallet installed on it, nothing else
For example you might have a laptop that runs the minimum install of Ubuntu together with Sparrow Wallet. That’s it. This laptop wouldn’t be used for anything else and wouldn’t have any other software installed on it.
The only time it ever gets turned on is to connect to your Hardware Wallet and receive or send transactions. This step hugely reduces the attack surfaces that are possible as there’s no longer 20 different apps installed, no random websites or files being opened and so on.
As said, the computer should be new enough to still get current security updates for whatever OS that it’s running. For example, a 8 year old Samsung phone isn’t going to be getting regular security updates and as such, wouldn’t be a good idea. A 10 years old laptop might be cheap, but if all it can run is Windows XP then it’s going to be a security nightmare.
Will this setup prevent every attack? No. But it adds a significant layer of protection to your overall security setup. Now hackers can send you phishing emails all day, completely compromise your daily driver computer and turn it into a malware invested dumpster fire. At the end of it they still won’t have any access or knowledge of your Bitcoin Wallet setup.
Proper security is about creating layers upon layers to slow down and or stop attackers. This is another important one and mitigates an enormous amount of potential attacks.
IRL Security Best Practices
Last but not least is your In Real Life (IRL) security. To be absolutely clear here, the best thing you can do to protect your physical security is simply just shut the hell up and be cool. Be anonymous and never signal to others anything you don’t absolutely have to. We covered this in our Advanced guide but anonymity is a super power, use it!
You can have 1,000,000 bitcoins that you carry around in your mobile hot wallet (like a complete moron) and no one would know unless you tell them.
Any time someone asks you about Bitcoin just play dumb, smile and nod. You don’t have any bitcoin, you might have bought $100 worth years ago but you sold them when it was going crazy and don’t have any now. In fact, you don’t really know much about it all. Next topic.
This silence extends online too. No posting about Bitcoin. No detailing of your funds. No detailing of your Node or wallet or software or setup or even just your general security at all! Doing this kind of shit is just reckless:
Guess what? Now people not only know that user XYZ has a Bitcoin node (and thus likely a decent amount of bitcoins) but also that they use the MyNode software, they know they run router ABC and can thus target phishing emails and cater their malware specifically to take advantage of security holes on those devices. We’ll say this again!
Never disclose any information about your funds or security. Ever!
In Person Attacks
Now let’s look at various attacks that have actually happened before to other unfortunate people. While obviously not a complete database, take a read over this list of Known Physical Bitcoin Attacks. Analysis of this (limited) list reveals three main types of physical attacks:
- In Person Trades (29%)
- Home / Work Invasion (29%)
- Kidnapping (25%)
While kidnapping was mainly in less secure countries such as Brazil or Russia, there were a few in prominent places such as New York. As a result, we can recommend a few key things to help avoid what seems to be the most common attack vectors:
- Avoid In Person Trades: They’re statistically more likely to involve physical attacks
- Keep Good Company: While not specific to Bitcoin, poor choice of associates statistically seems to lead to more physical attacks
You’ll notice that in all three of the most common cases the attackers knew that the person had bitcoins on them or believed that they had access to them at home or work and thus, tried to take advantage of it. This reiterates just how vital being anonymous is or at the very least, ensuring that your real world identity isn’t tied to having bitcoins.
When it comes to trading and buying bitcoins it’s why we so strongly demand complete anonymity. Even if you buy bitcoins online, if they’re tied to your real world address that data will leak and now you’re physically at risk essentially forever. Don’t be stupid and only buy bitcoins via non-KYC Crypto Exchanges.
Other recommendations for ensuring your physical safety includes:
- Avoid Wealth Signalling: No lambos, Rolex, wads of cash, mansions etc
- Avoid Bitcoin Signalling: No Bitcoin stickers, key chains, coffee mugs, t-shirts etc
- Enhance Home Security: Get security cameras, security doors, bigger locks, dogs etc
- Enhance Personal Security: Learn how to fight, increase situational awareness, practice etc
These things can obviously be done in stages and are more “ongoing” measures that you can enact over time. But always be mindful about what information you’re giving away. From subscribing to a Bitcoin focused newsletter with email addresses that are linked to your real world identity to something as simple as a sticker. The goal is to give nothing away.